TCMS - Thin Client Access Gateway (VPN)
The Rangee Thin Client Management Server (TCMS) can be used as a gateway to connect externally operated Rangee Thin Clients to your network. This HowTo describes the necessary configuration steps.
Prerequisites
To utilize the TCMS VPN functionality, the following prerequisites must be met:
- The Thin Client with RangeeOS must have the "tcmsclient-vpn" license. If you don't have a license for the module yet, you can purchase one through our sales department or via our contact form or request a 30-day demo license .
- The TCMS must be reachable via a fixed IP or hostname.
- The TCMS must be reachable by both the chosen registration port and the chosen VPN port for the clients.
- The servers that the clients should be reachable through the TCMS must be reachable by the TCMS.
Configuration
TCMS
Configuring an Additional TCMS API Port
By configuring an additional TCMS API port, you can define a port through which only Thin Clients can connect to the TCMS, while the web interface is not available. Using the additional API port is highly recommended when making the TCMS available over the internet.
You can configure the additional API port in the TCMS under Edit -> Settings -> Base Settings . Here are the options:
- Additional API Port - Freely selectable TCP port, in our example 8888.
- Allow Repository Access via Additional API Port (optional) - Allows clients to receive updates from the TCMS repository via this port.
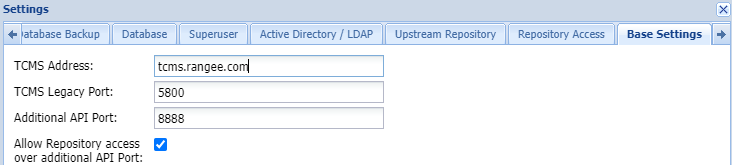
TCMS - Base Settings
Configuring the TCMS VPN Connection
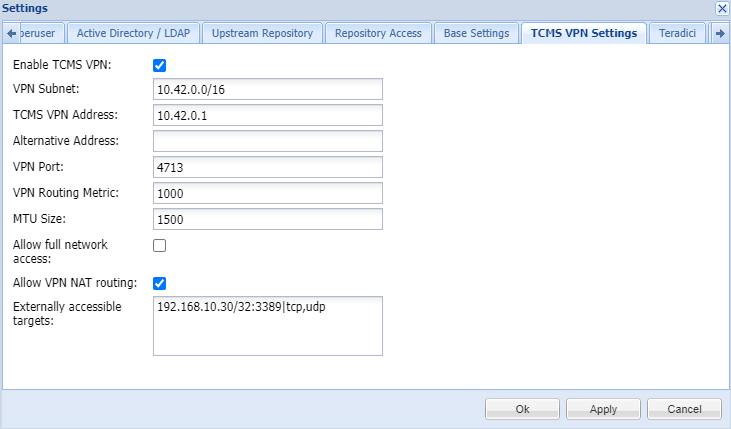
You can find the TCMS VPN configuration under Edit -> Settings -> TCMS VPN Settings . Here are the following options:
- Enable TCMS VPN - Activates the TCMS VPN service.
- VPN Subnet - Defines an internal TCMS-VPN-CLIENT subnet in CIDR form. This network should not overlap with your internal network.
- TCMS VPN Address - Address of the TCMS server within the VPN subnet.
- VPN Port - UDP port over which the VPN connection should be established. Must be made externally available.
- VPN Route Metric - Determines the metric with which the VPN connection is established on the client side.
- Allow VPN NAT routing - When enabled, this option allows VPN-connected clients to access servers defined under Externally accessible targets.
- Externally accessible targets - In this text field, any targets for VPN-connected clients can be made available. The following notations must be used, where only the specification of the server/subnet is mandatory:
#Server/Subnet in CIDR form#:#Port#,#Port2#|#Protocol1#,#Protocol2#
Examples:- 192.168.10.30/32 or 192.168.10.30
Allows access to all ports on the server with IP 192.168.10.30. - 192.168.10.0/24
Allows access to all machines in subnet 192.168.10.0/24. - 192.168.10.30/32:3389
Allows access to the server with IP 192.168.10.30 only on port 3389. - 192.168.10.30/32:443,4712
Allows access to the server with IP 192.168.10.30 on ports 443 and 4712. - 192.168.10.0/24:3389|tcp
Allows access to all machines in subnet 192.168.10.0/24 on port 3389 TCP. - 192.168.0.0/16:443|tcp,udp,icmp
Allows access to all machines in subnet 192.168.0.0/16 on port 443 TCP, UDP, and ICMP (Ping).
- 192.168.10.30/32 or 192.168.10.30
TCMS VPN Settings
Specifying VPN Clients
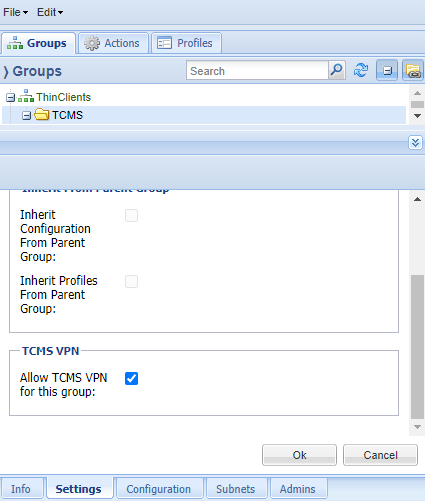
The specification of which clients should use the TCMS VPN configuration is done through a group setting.
To do this, select the group in the Groups tab for which you want to enable TCMS-VPN. Then, enable the "Allow TCMS VPN for this group" option in the Settings tab of the group.
Activate VPN Connection for Group
Thin Client
On the Thin Client side, no special configuration is required to use the TCMS VPN connection. The client receives all necessary data for this from its TCMS configuration.
However, ensure that the client establishes its connection to the TCMS via the Additional API Port and the externally resolvable hostname or fixed IP address. You can find the setting in the client's Kommbox under Remote Administration -> TCMS Settings .
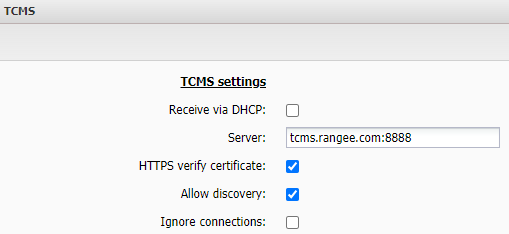
TCMS Settings on Thin Client Side
Firewall
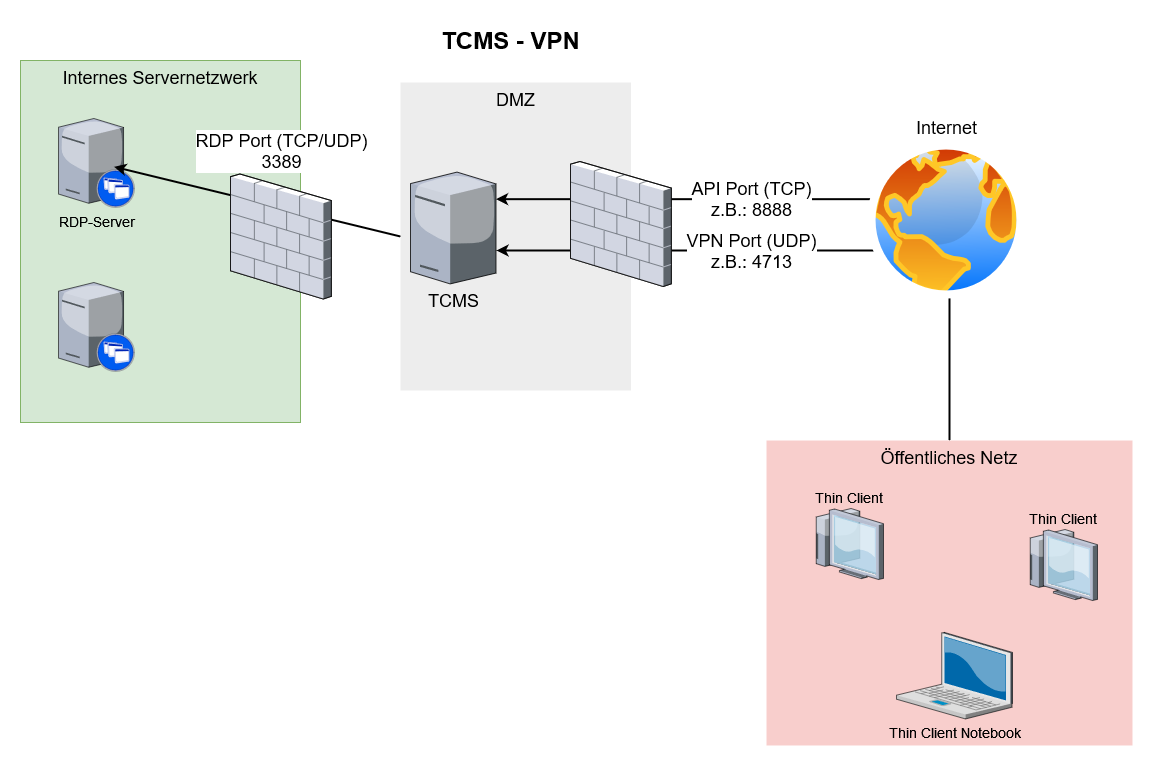
On the firewall side, appropriate rules must be defined for the ports you have chosen.
Example configuration for allowing an RDP server:
- TCMS:
- IP in DMZ: 10.10.10.5
- API Port 8888
- VPN Port 4713
- RDP Server:
- IP in Internal Network: 192.168.10.30
For this example configuration, the following rules must be created in your firewall(s):
- DNAT/Allow from Internet to Port 8888 (TCP) to TCMS (DMZ/10.10.10.5)
2. DNAT/Allow from Internet to Port 4713 (UDP) to TCMS (DMZ/10.10.10.5)
3. DNAT/Allow from TCMS to Port 3389 (TCP/UDP) to RDP Server (Internal/192.168.10.30)