RangeeOS - Configuration de Microsoft Defender
Il est possible d’installer et de configurer Microsoft Defender for Endpoint sous RangeeOS.
Installation
Installez sur votre Thin Client ou TCMS le module logiciel microsoft-defender_24082.0001-x64.
Des informations sur l’installation des mises à jour sont disponibles ici : RangeeOS - Firmware13 - Update / Upgrade / Downgrade
Si le module logiciel n’est pas encore proposé en téléchargement, veuillez contacter : support@rangee.com pour l’activation.
Configuration
Après l’installation, vous pouvez configurer Defender via Connexions & Applications → Microsoft Defender for Endpoint.
Onboarding
Pour intégrer le client à votre environnement Defender, vous aurez besoin du package d’onboarding disponible sur le portail Microsoft Defender :
https://learn.microsoft.com/de-de/defender-endpoint/linux-install-with-ansible#download-the-onboarding-package-applicable-to-both-the-methods
Le fichier ZIP téléchargé contient le fichier "MicrosoftDefenderATPOnboardingLinuxServer.py". Téléchargez ce fichier sur votre appareil via l’option correspondante.
Cette étape doit être répétée sur chaque appareil où Defender doit être utilisé.
Après un onboarding réussi, le statut actuel de Defender s’affiche sous "Informations":
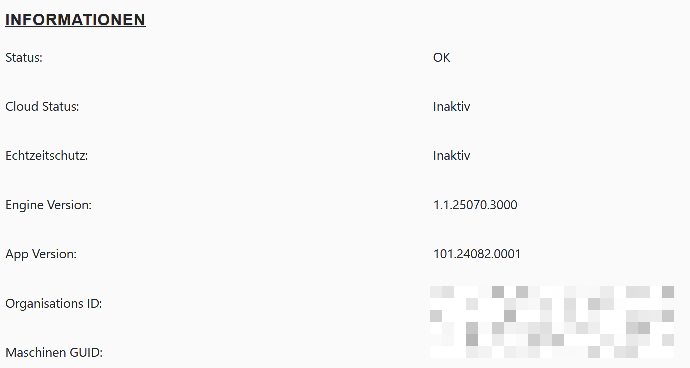
Le client/TCMS apparaît ensuite en ligne dans le Microsoft Security Center environ 5 à 20 minutes après l’onboarding.
Options
Une fois le client onboardé, vous pouvez effectuer les actions suivantes sous Connexions & Applications → Microsoft Defender for Endpoint :
- Activer Microsoft Defender for Endpoint : active le service Defender
- Activer la protection cloud
- Activer la collecte des données de diagnostic cloud
- Activer la protection en temps réel
- Désenregistrer l’appareil : supprime la configuration Defender (offboarding)
- Fichier journal : affiche le journal du dernier scan
- Analyse rapide : effectue un scan rapide du système
- Analyse complète : effectue un scan complet du système
Les alertes sur les détections et événements inhabituels sont également signalées dans le portail Microsoft Security.
